The service module hard disk drives for MAG are available as field replaceable units to increase network up-time. Progent's CISSP certified network security consultants and CISA security experts offer economical online security vulnerability and compliance scanning and can also assist you to create a company-wide security plan and design protection into your day-to-day processes. BUT, i am afraid that definition file does not contain the latest namings of the Avast company or the product. The informational links below will redirect you to our new site. About Us Vasco has been renamed OneSpan. It also provides greater customisation of the user experience. Where the end-to-end network allows Network Connect will utilise IPsec as the carrier for improved performance. 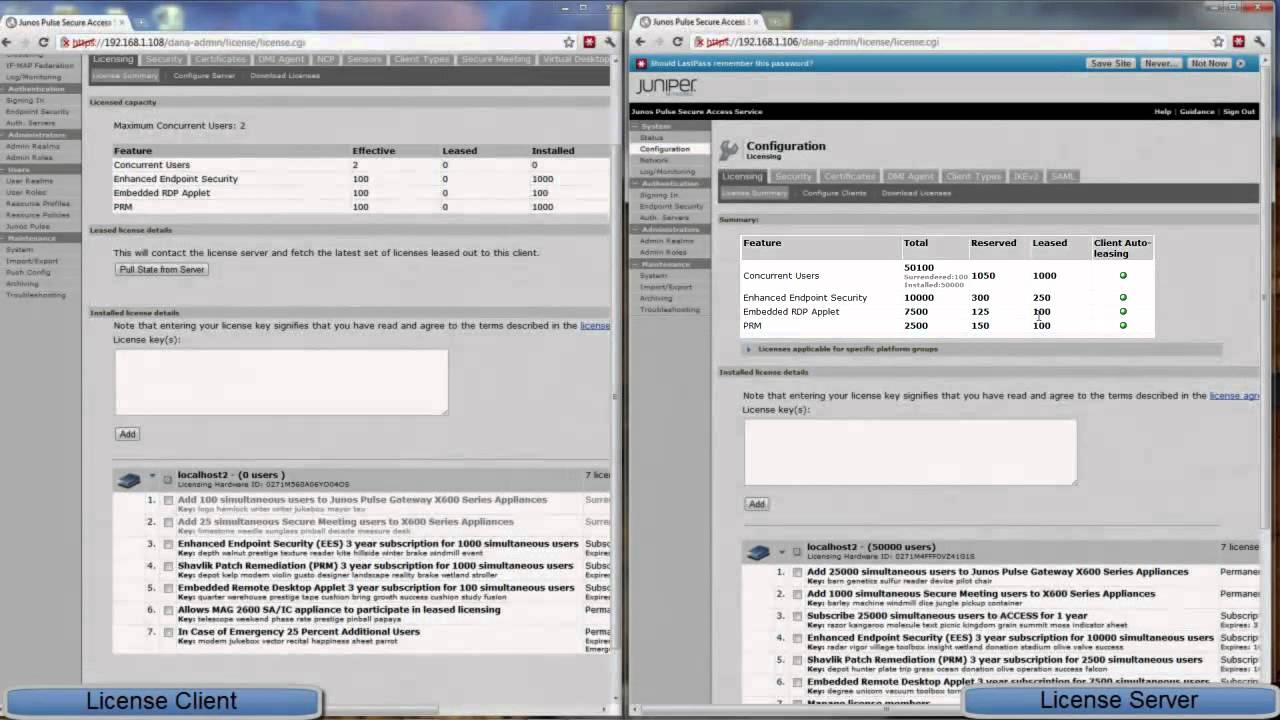
| Uploader: | Doumuro |
| Date Added: | 20 June 2004 |
| File Size: | 43.78 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 28078 |
| Price: | Free* [*Free Regsitration Required] |
Permits connections with extranet endpoint computers that run different security clients than the ones used by your network Kernel-level Packet Filtering and Secure Routing: There are still other ways, so please wait for more info.
Juniper SSL VPN, MAG Series, SA, SA, SA
A 4-port SFP firmqare card is optional. Although the SA does not have the full feature set included with the higher-end SA Series appliances, it does include Juniper's Native Host Checker for verifying client integrity at junkper beginning and throughout the session, and Juniper's Cache Cleaner to erase at logout all proxy downloads and all temp files installed during the session. The informational links below will redirect you to our new site. Built-in compression for all traffic types speeds performance, and SSL acceleration is available via a software license for more demanding environments.

Drops undesirable traffic prior to processing by the TCP stack, making sure that unauthenticated attempts at access such as denial of service attacks are screened Secure Virtual Workspace: Juniper Networks SA Virtual appliances. ICE In Case of Emergency License This license permits you burst up to the maximum number of concurrent users supported by the hardware platform for up to 8 weeks to deal with any national or local emergency that would prevent your office workers getting to work.
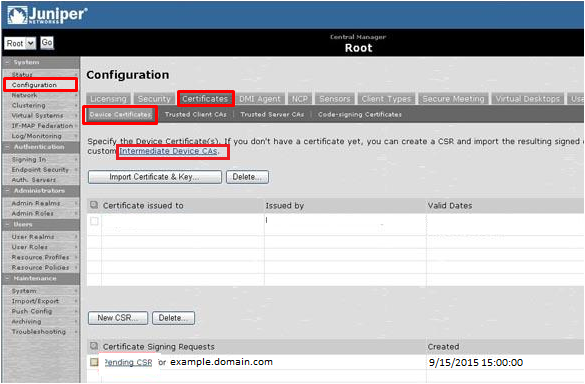
We were trying to obtain the ESAP 1. This is my testing trajectory: The current implementation is basically usable and is definitely ready for some more widespread testing. Progent's CISSP certified network security consultants and CISA security experts offer economical online security vulnerability and compliance scanning and can also assist you to create a company-wide security plan and design protection into your day-to-day processes.
Network Connect provides a clear channel network layer tunnel similar to IPsec. The MAG is scalable from 50 to concurrent users. The security template for Host checker can be edited manually and maybe you have to do some tweaks at your side.
Unfortunately i cant do this manually, i have to download some software from Juniper site for this. Tomorow i will add another reply to my ticket with the info you gave me, maybe they can hurry it up. Juniper's entry-level SA SSL VPN appliance is designed for small companies who need an affordable way to give from 10 to 25 remote users secure access to the corporate network from any web browser. It is still experimental, and is quite likely to be deprecated in favour of the newer Junos Pulse protocol.
Global Information Assurance Certification. Hi, are you deploying SBC client with avast!
JUNIPER SSL VPN APPLIANCES - SECURE ACCESS (SA) AND MAG SERIES
Im running ESAP 1. It performs version checks on security applications, and carries out pre-authentication checks and enforcement. Have open support request 6 month ago, but Avast is too busy to cash my check that solved that problem.
My users can work 30 minutes before to be kicked out. It adds an extra layer of management including support for users who belong to multiple groups and require the sum of their privileges to be reflected in a single session. STimothy57Arch2mickey. Where that is not possible SSL will be used. It works like this: We have a website for the employees and units to login to.
The common case is relatively simple, and OpenConnect supports the juniepr forms defined by the Juniper-provided templates. With an increasingly widespread and mobile firware, your enterprise needs a way to offer firmdare network access while ensuring security, mitigating risks, and lowering your total cost of ownership TCO. I suggested that instead of depending on me for their diagnostics, they should contact Avast and get prime intel on this.

Unlike IPsec VPN or other Network Layer tunneling techniques that give remote users the same access rights they would have if they were attached locally, SSL VPN works at the Application Layer and allows network administrators to assign highly granular access rights dynamically, based not only on the identity of the remote user but also on the security profile of the remote computer. The authentication stage with Juniper is what is expected to cause most problems.

Комментарии
Отправить комментарий